
Hacking & Securing PHP Applications
.MP4, AVC, 1000 kbps, 1280×720 | English, AAC, 64 kbps, 2 Ch | 66 Lectures | 463 MB
Provider: Cyber Security & Privacy Foundation
This course teaches how to hack and secure PHP. Owasp top10(A1 to A10) for PHP.
This course teaches the programmers on how to exploit(hack) and defend against various attacks on PHP language. The course is designed around OWASP Top10 which is common standard which is used in design, architecture, testing of web applications.
The course contains video/audio lectures. It has Theory on PHP programming(Exploit, Defense) . It also has Demos of exploitation and Defense. It gives students practical insight into coding web application in PHP securely.
We recommend students to study the course over a period of 15 days and attempt the quiz at the end of the period. we also recommend students to study various resource material available on the internet in various forums including OWASP official website.
The course is structured according to OWASP Top 10 from A1 to A10. In each of the OWASP Top10 sessions we have categorized presentation, exploitation, defense.
Any programmer who is programming in PHP, should take this course. Secure PHP programmers are prefered by organisations across the globe.
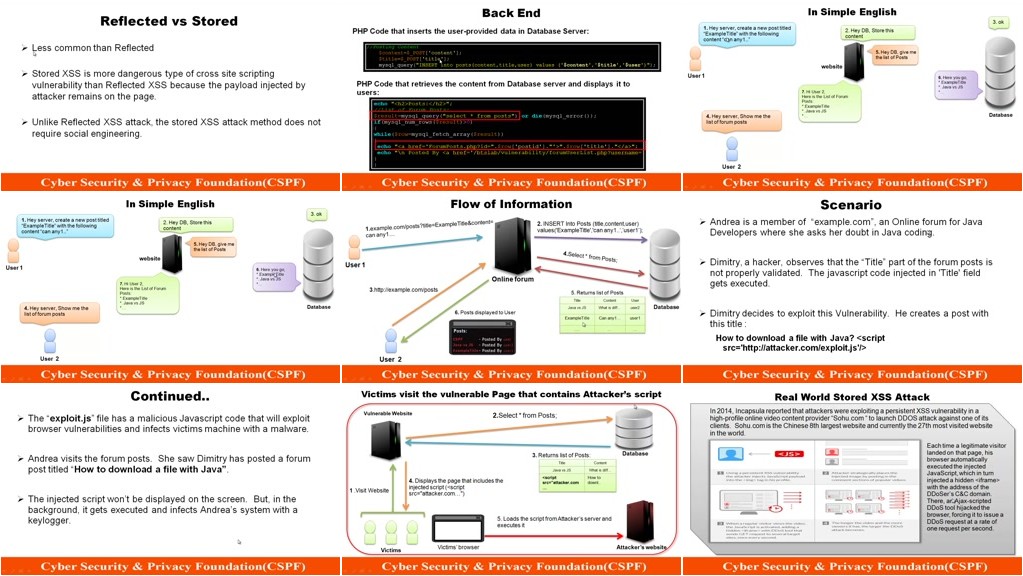
This course teaches the programmers on how to exploit(hack) and defend against various attacks on PHP language. The course is designed around OWASP Top10 which is common standard which is used in design, architecture, testing of web applications.
The course contains video/audio lectures. It has Theory on PHP programming(Exploit, Defense) . It also has Demos of exploitation and Defense. It gives students practical insight into coding web application in PHP securely.
We recommend students to study the course over a period of 15 days and attempt the quiz at the end of the period. we also recommend students to study various resource material available on the internet in various forums including OWASP official website.
The course is structured according to OWASP Top 10 from A1 to A10. In each of the OWASP Top10 sessions we have categorized presentation, exploitation, defense.
Any programmer who is programming in PHP, should take this course. Secure PHP programmers are prefered by organisations across the globe.

Download uploaded
http://uploaded.net/file/u1uzuai2/HackingAndSecuringPHPApplications.part1.rar
http://uploaded.net/file/nme4q771/HackingAndSecuringPHPApplications.part2.rar
http://uploaded.net/file/l49ue4uw/HackingAndSecuringPHPApplications.part3.rar
http://uploaded.net/file/u1uzuai2/HackingAndSecuringPHPApplications.part1.rar
http://uploaded.net/file/nme4q771/HackingAndSecuringPHPApplications.part2.rar
http://uploaded.net/file/l49ue4uw/HackingAndSecuringPHPApplications.part3.rar
Download nitroflare
http://www.nitroflare.com/view/73BEF769B74DA61/HackingAndSecuringPHPApplications.part1.rar
http://www.nitroflare.com/view/31BFA7868995027/HackingAndSecuringPHPApplications.part2.rar
http://www.nitroflare.com/view/7308216032D27E3/HackingAndSecuringPHPApplications.part3.rar
Download rapidgator
http://rg.to/file/05575e1c393f3e449f26c458e0021439/HackingAndSecuringPHPApplications.part1.rar.html
http://rg.to/file/9c3626b46f406394849bb1edfd3a5cc4/HackingAndSecuringPHPApplications.part2.rar.html
http://rg.to/file/7dd327168d3302d7eda42f08f2b49b26/HackingAndSecuringPHPApplications.part3.rar.html
Download 百度云
链接: http://pan.baidu.com/s/1jGlAwnk 密码: yeia