
English | mp4 | H264 1280×720 | AAC 2 ch | pdf | 6.43 GB
eLearning
This course will familiarize students with all aspects of Linux forensics. By the end of this course students will be able to perform live analysis, capture volatile data, make images of media, analyze filesystems, analyze network traffic, analyze files, perform memory analysis, and analyze malware all on a Linux system with readily available free and open source tools. Students will also gain an in-depth understanding of how Linux works under the covers.
A non-exhaustive list of topics to be covered includes:
Live response
– First talk to the humans
– What do they think happened
– Details on victim system(s)
– Mount response kit with known good tools
– cdrom preferred as it was not likely part of compromise
– USB MS can be used if no CDROM
– Using netcat to minimize contamination
– Collecting volatile data
– date and time
– network interfaces
–– funny networks
–– promiscuous mode?
– network connections
– open ports
– programs associated with ports
– running processes
– open files
– routing tables
– mounted filesystems
– loaded kernel modules
– Collecting data to determine if dead analysis is justified
– kernel version
– uptime
– filesystem datetime stamps
– hash values for system files
– current user logins
– login history
– system logs
– user accounts
– user history files
– hidden files and directories
– sending off suspicious files for further study
– Dumping RAM
– Making the decision to dump RAM
– Using fmem
– Using LiME
– Using /proc/kcore
Acquiring filesystem images
– Using dd
– Using dcfldd
– Write blocking options
– Forensic Linux distros
– Udev rules based blocker
Analyzing filesystem images
– Mounting images
– Files with basic system info
– Files with suspicious user info
– Examining logs
– Process-related files
– Authentication-related files
– Using standard Linux tools to find information
– Strange files
– – Regular files in /dev
– – User history files
– – Hidden files
– – SUID/SGID files
– – Detecting backdated files
– Recovering deleted files
– – Finding deleted files
– – Attempting recovery
Leveraging The Sleuth Kit (TSK) and Autopsy
– mmls
– fsstat
– dstat
– istat
– fls & mactime
Timeline Analysis
– When was system installed, upgraded, booted, etc.
– Newly created files (malware)
– Changed files (trojans)
– Files in the wrong place (exfiltration)
Digging deeper into Linux filesystems
– Disk editors
– – [email protected] Disk Editor
– – Autopsy
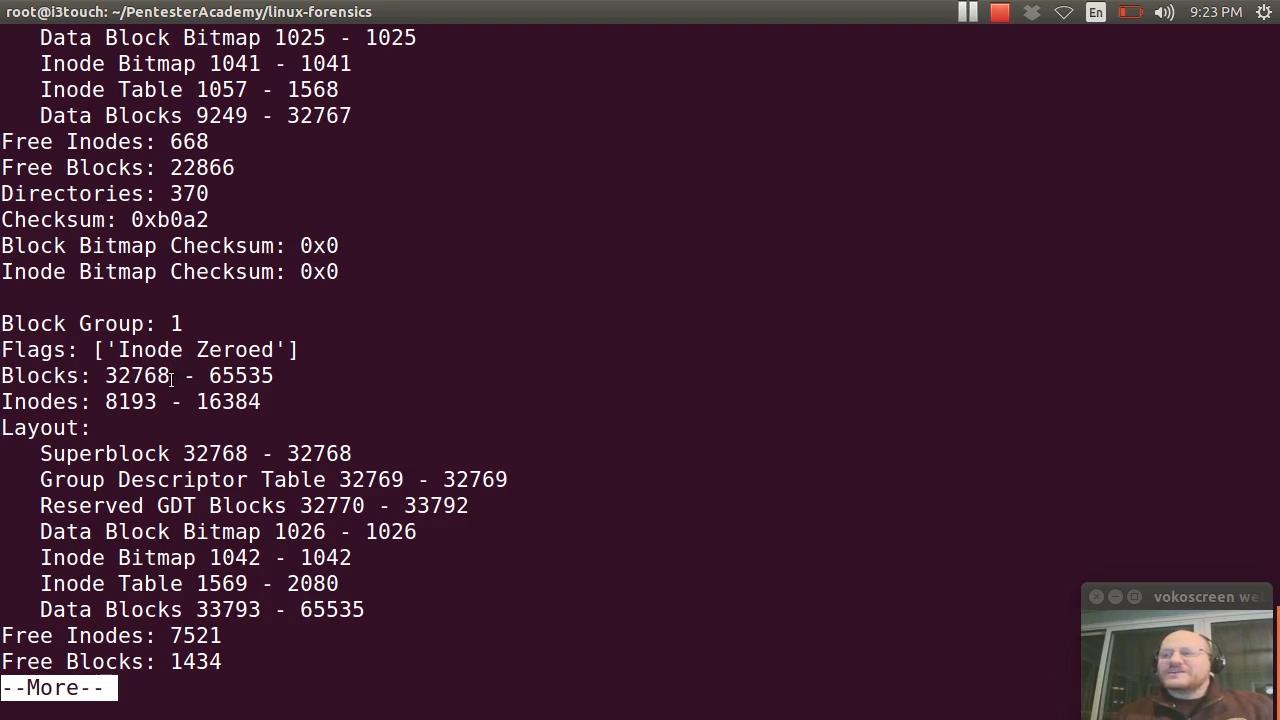
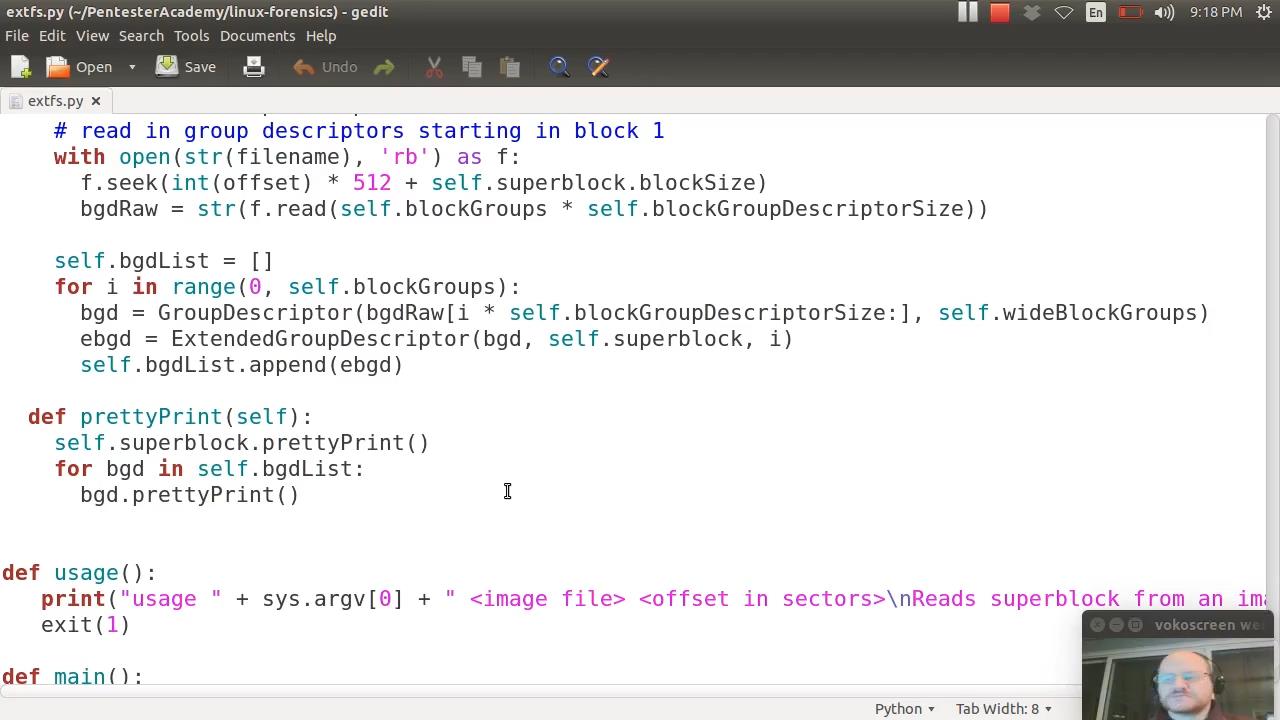
– ExtX
– – Basics
– – – Superblocks
– – – Directory entries
– – – Inodes
– – – Data blocks
– Compatible, incompatible, and read-only compatible features
– Experimental features may be installed
– Boot code
– Using sigfind to find important blocks
– Understanding indirect block levels
– istat, ils, ifind, icat
– Links and mounts
– Hash trees
– Journaling
– – jls
– – jcat
– Finding data with blkstat, blkls, blkfind, blkid, and blkcalc
– Relating data found with grep to a file/application
– – Finding block size, etc.
– – Using grep with a keyword file
– – Seeing data in context
– – Associating a file with the data
– Undeleting files
– Searching unallocated space
Network forensics
– Using snort on packet captures
– Using tcpstat
– Seperating conversations with tcpflow
– Tracing backdoors with tcpflow
File forensics
– Using file signatures
– Searching through swap space
– Web browsing reconstruction
– – Cookies
– – Search history
– – Browser caches
– Unknown files
– – Comparing hashes to know values
– – File command
– – Strings command
– – Viewing symbols with nm
– Reading ELF files
– objdump
– Bringing out big guns – gdb
Memory Forensics
– Volatility Profiles
– Retrieving process information
– Recovering command line arguments
– Rebuilding environment variables
– Listing open files
– Retrieving bash information
– Reconstructing network artifacts
– Kernel information
– Volatile file system information
– Detecting user mode rootkits
– Detecting kernel rootkits
Reversing Linux Malware
– Digging deeper into ELF
– – Headers
– – Sections
– – Strings
– Symbol tables
– Program headers
– Program loading
– Dynamic linking
Command line analysis tools
– strings
– strace
– ltrace
Running malware (carefully)
– Virtual machine setup
– Capturing network traffic
– Leveraging gdb
Writing the reports
– Autopsy
– Dradis
– OpenOffice
Download uploaded
http://uploaded.net/file/kf92oml3/LiFornsics.part01.rar
http://uploaded.net/file/mlvr5u90/LiFornsics.part02.rar
http://uploaded.net/file/muymzm09/LiFornsics.part03.rar
http://uploaded.net/file/4wfk1gmx/LiFornsics.part04.rar
http://uploaded.net/file/74a82p6d/LiFornsics.part05.rar
http://uploaded.net/file/peqf490b/LiFornsics.part06.rar
http://uploaded.net/file/dw05okob/LiFornsics.part07.rar
http://uploaded.net/file/cz6hv0ui/LiFornsics.part08.rar
http://uploaded.net/file/9td0xw5i/LiFornsics.part09.rar
Download nitroflare
http://nitroflare.com/view/DBAFD40330B0286/LiFornsics.part01.rar
http://nitroflare.com/view/456B8B32BB58518/LiFornsics.part02.rar
http://nitroflare.com/view/56E83FB9667FDAB/LiFornsics.part03.rar
http://nitroflare.com/view/993D03E627576B2/LiFornsics.part04.rar
http://nitroflare.com/view/104C08B8E483681/LiFornsics.part05.rar
http://nitroflare.com/view/DE2ACAEDFE07A69/LiFornsics.part06.rar
http://nitroflare.com/view/0E843EF9EACEBCA/LiFornsics.part07.rar
http://nitroflare.com/view/4C542062AC8A7C2/LiFornsics.part08.rar
http://nitroflare.com/view/B7EC5B7FEE405E8/LiFornsics.part09.rar
Download 百度云
你是VIP 1个月(1 month)赞助会员,