
Cybrary IT – Social Engineering and Manipulation
English | mp4 | H264 1280×720 | AAC 2 ch | pdf | 1.23 GB
eLearning
Get started with Social Engineering by viewing the course videos below. The intro to social engineering course covers, exploitation lifecycle, digital information gathering, targeting, digital profile reduction, elicitation, and more.
Social Engineering and Manipulation – Exploitation of the Human Element
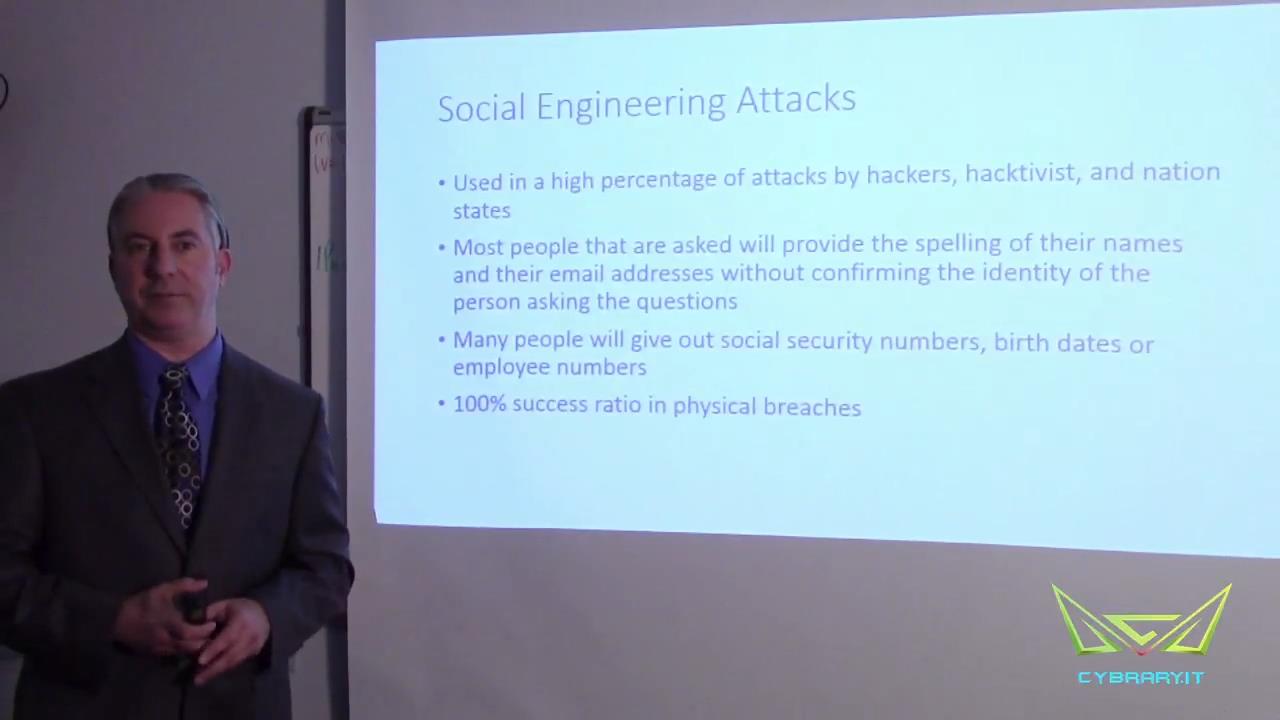
Social engineering has been the cause of many of the most high profile cyber-attacks in recent years.
The human element is too often the problem. In this online, self-paced Social Engineering and Manipulation training class, you will learn how some of the most elegant social engineering attacks take place. Learn to perform these scenarios and what is done during each step of the attack, from imitation through exploitation.
This course is intended to help you better prepare your organization for defense of social engineering attacks, as well as how to ethically use these techniques for intelligence gathering. As a reminder, by taking this course, you agree to our terms of service.
Topics include: Intro to social engineering, exploitation lifecycle, digital information gathering, targeting, digital profile reduction, psychology of social engineering, elicitation, pretexting, cold calling, bypassing physical security, post exploitation, binary evasion and more.
Tools include: Kali Linux, Social Engineering Toolkit (SET), Google, Maltego, Scythe Framework, Recon-NG Framework, Creepy, Portable Virtual Box, Metasploit, Hyperion & Veil
Pre-requisites: This class is intended for cyber security professionals who have at least a baseline understanding of penetration testing and security policy principles. Approximately two years of experience in cyber security or Certified Ethical Hacker certification (or comparable cert) is highly recommended. If you do not meet these pre-requisites, it is recommended that you complete our Security+ and Ethical Hacker classes, before beginning.
Download uploaded
http://uploaded.net/file/k7tuity7/SocEngineerandMan.part1.rar
http://uploaded.net/file/ksabrgb8/SocEngineerandMan.part2.rar
http://uploaded.net/file/5y9sjmpl/SocEngineerandMan.part3.rar
Download nitroflare
http://nitroflare.com/view/AEB9C5773B95255/SocEngineerandMan.part1.rar
http://nitroflare.com/view/66C492594F521FC/SocEngineerandMan.part2.rar
http://nitroflare.com/view/6B049FDCE5D5C46/SocEngineerandMan.part3.rar
Download 百度云
你是VIP 1个月(1 month)赞助会员,
转载请注明:0daytown » Cybrary IT – Social Engineering and Manipulation

