
Exploiting Android Apps for beginners – Check Apps Security (2015)
WEBRip | MP4/AVC, ~3544 kb/s | 1282 x 720 | English: AAC, 59.3 kb/s (2 ch), 44.1 KHz | 1.62 GB
Genre: IT & Software / Network & Security | Language: English | +Project Files
Has the right balance of theory and hands-on. Good set of tools discussed. Offered by leaders in Mobile App Security.
If you at any point of time in your career or academia surfaced information security, you know for a fact that security analysis is not only about thorough understanding of a system but also includes a good list of tools and techniques to analyze that particular system. Unlike network and web, mobile security is a recent phenomenon. In order to analyze mobile application, one should understand the underlying architecture, security model, development frameworks and the relevant tools.
This course deals with applications within the most widely used mobile OS, Android. The course introduces underlying Android architecture, its permission model and the default security measures in place. It deals with developer tools like Eclipse, Android Studio, Android Debug Bridge or ADB, UI Automator and Monkey Runner, along with tools and techniques for Network Analysis.
As a part of reversing and malware analysis, static and dynamic techniques have been discussed. Pentesting an Android App is has also been discussed. Issues like unintended data leakage, insecure data storage and tools like Burp Intruder & Metasploit have also been covered. The course concludes by discussing Android best practices for security.
To conclude, this course deals with Android security concepts and discusses the relevant tools in detail to exploit an Android application.
What are the requirements?
- Android Dev Environment
- Linux OS
What am I going to get from this course?
- Over 68 lectures and 10 hours of content!
- Understand Android’s Architecture and Security Model
- Get familiar with tools for development, reverse engineering and security analysis
- Pentesting Android Apps
What is the target audience?
- Existing security professional trying to get into Mobile App Security in general and Android security in personal
- Students in Security specialization
- Android developers
- Members of QA team testing Android Apps
Curriculum
Section 1: Introduction
Lecture 1 Importance of Information Security 07:14
Lecture 2 Mobile First and State of the Art Product Design 07:36
Lecture 3 Need for Mobile Security and OWASP Top 10 10:21
Lecture 4 Basic Terminologies in Information Security 08:47
Lecture 5 About CIA Triad 07:04
Lecture 6 Introduction to Cryptography 11:46
Lecture 7 Hashing and Digital Signature 13:53
Lecture 8 Digital Certificates and PKI 12:59
Lecture 9 TLS_SSL_Protocol and Handshake Process 06:57
Lecture 10 DoS and DDoS attack 07:42
Lecture 11 AAA 07:50
Lecture 12 Password Security 07:44
Lecture 13 Access Control 04:40
Section 2: Android Architecture and Security Model
Lecture 14 A Brief about Android 11:52
Lecture 15 Android Bootup Process 07:27
Lecture 16 Android Architecture 07:54
Lecture 17 Android Data Structure and File system 13:24
Lecture 18 Android Logging and Logcat 13:48
Lecture 19 Android Apps 07:08
Lecture 20 Android Security Model 10:42
Lecture 21 Android Permissions 08:53
Lecture 22 Security Compliance w.r.t. Android Framework and Java 07:24
Lecture 23 Google Bouncer 04:29
Section 3: Getting Familiar with Android Developer Tools
Lecture 24 Eclipse IDE and Andorid Studio 19:15
Lecture 25 Android Debug Bridge 06:42
Lecture 26 UIAutomator and MonkeyRunner 11:40
Section 4: Interacting with an Android Device
Lecture 27 Difference between an Android device and an Emulator 04:42
Lecture 28 Interacting with Android device via USB 04:02
Lecture 29 SSH 06:51
Lecture 30 VNC 06:54
Lecture 31 Rooting Android Device 08:59
Lecture 32 BusyBox 05:30
Section 5: Android Network Analysis
Lecture 33 Setting up a Proxy for Android Emulator 05:54
Lecture 34 Setting Up a Proxy for Android Device 04:52
Lecture 35 Installing CA Certificate 06:44
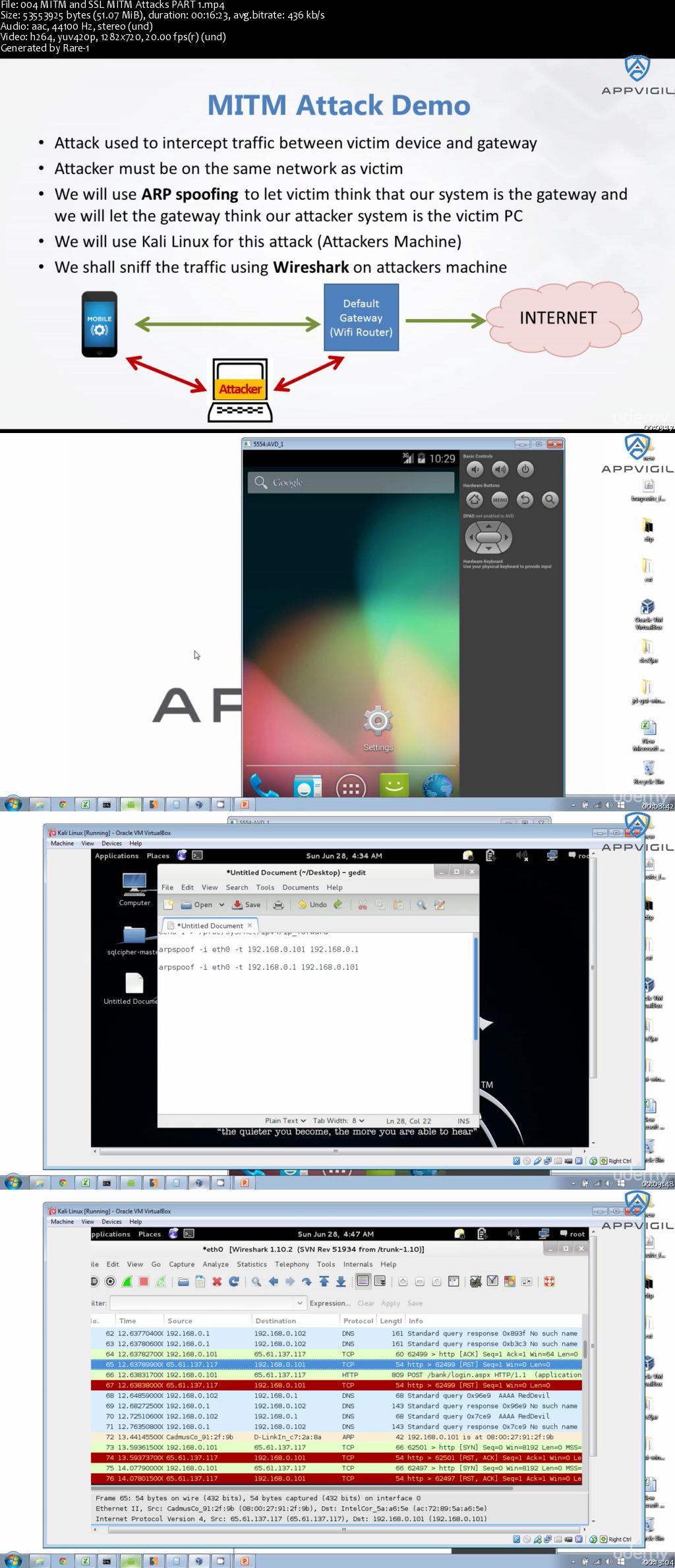
Lecture 36 MITM and SSL MITM Attacks: PART 1 16:23
Lecture 37 MITM and SSL MITM attacks PART 2 09:15
Lecture 38 Data Manipulation 06:13
Section 6: Android Reversing and Malware Analysis
Lecture 39 APK Files in a Nut Shell 10:49
Lecture 40 Intro to Reverse Engineering 06:52
Lecture 41 Reversing to Get the Source Code 07:25
Lecture 42 Using APKTool for Reverse Engineering 09:26
Lecture 43 Introduction to Android Malwares 09:04
Lecture 44 Dynamic vs Static Analysis 04:08
Lecture 45 Static Analysis of Android Malwares 17:58
Lecture 46 Introduction to Android Tamer 06:07
Lecture 47 Dynamic Analysis with DroidBox 08:23
Lecture 48 Dynamic Analysis of Android Malwares 10:11
Section 7: Android Application Pentesting and Exploitation
Lecture 49 Introduction to Android Pentests 04:32
Lecture 50 Fuzzing Android Apps with Burp Proxy 04:52
Lecture 51 Fuzzing Android Apps with Burp Intruder 11:44
Lecture 52 Attacking authentication 08:00
Lecture 53 Content Provider Leakage 10:25
Lecture 54 Client Side Injection 08:14
Lecture 55 Insecure Data Storage – Shared Preferences 08:52
Lecture 56 Insecure Data Storage – SQLite Databases 08:11
Lecture 57 Unintended Data Leakage 10:30
Lecture 58 Broken Cryptography 15:17
Lecture 59 Automated Security Assessments with Drozer 14:37
Lecture 60 Exploiting Android Devices Using Metasploit 12:04
Section 8: Android Device and Data Security
Lecture 61 Android Device Protection 06:43
Lecture 62 Bypassing Android Locks 10:46
Lecture 63 Android Data Extraction 09:19
Section 9: Using Android as a Pentesting Tool
Lecture 64 A Look into Commonly used Hacking and Pentesting Apps 10:59
Lecture 65 PWN Pad on Nexus 7 04:47
Lecture 66 Kali Linux on Android 04:01
Section 10: Conclusion
Lecture 67 Android Security Practices 08:22
Lecture 68 Course Summary and Revision 05:30
Download uploaded
http://uploaded.net/file/m53cf1oc/how-to-hack-android-apps.part1.rar
http://uploaded.net/file/793d8a8k/how-to-hack-android-apps.part2.rar
http://uploaded.net/file/ghmosyhq/how-to-hack-android-apps.part3.rar
http://uploaded.net/file/kw7r1hlp/how-to-hack-android-apps.part4.rar
http://uploaded.net/file/w6mft8y5/how-to-hack-android-apps.part5.rar
http://uploaded.net/file/zpc2axx0/how-to-hack-android-apps.part6.rar
http://uploaded.net/file/m0fvjdwk/how-to-hack-android-apps.part7.rar
Download nitroflare
http://www.nitroflare.com/view/D810CB4A078CC1B/how-to-hack-android-apps.part1.rar
http://www.nitroflare.com/view/A61CFA6238F5B91/how-to-hack-android-apps.part2.rar
http://www.nitroflare.com/view/56619F989A725FA/how-to-hack-android-apps.part3.rar
http://www.nitroflare.com/view/E1CF14DABA78A95/how-to-hack-android-apps.part4.rar
http://www.nitroflare.com/view/C42B20564C47800/how-to-hack-android-apps.part5.rar
http://www.nitroflare.com/view/19C8AADA58D045A/how-to-hack-android-apps.part6.rar
http://www.nitroflare.com/view/8F0D24821CDB92B/how-to-hack-android-apps.part7.rar
Download 百度云
你是VIP 1个月(1 month)赞助会员,
转载请注明:0daytown » Exploiting Android Apps for beginners – Check Apps Security (2015)