
MP4 | Video: h264, 1280×720 | Audio: AAC, 44.1 KHz, 2 Ch
Genre: eLearning | Language: English + .VTT | Duration: 67 hours | Size: 24.7 GB
What you’ll learn
550 detailed & 66+ hours of on-demand video about Cyber Security
Complete Certified Ethical Hacking training course from Scratch
Step by step instruction with practical & real world examples without neglecting the theory
Installing Kali Linux – a penetration testing operating system
Install windows & vulnerable operating systems as virtual machines for testing
Installing Android operating system as virtual machine for testing
Learn Linux commands and how to interact with the terminal
Learn linux basics
Learn to be anonymous when doing hacking and penetration testing activities
Gather passive & active information using different tools & techniques
Gathering Information about the target weather it is a person, website or a company
Learn to hack Wi-Fi NETWORK weather it is using WEP/WPA/WPA2
Disconnecting any device from the network
Create Rogue access point
Create Fake Captive Portals
Covering our tracks after cracking Wi-Fi network
Scanning the Network
Scanning for finding Vulnerabilities
Learn to Scan using different tools & techniques
Learn to Scan outside of your Network
Understand Denial of Service & Distributed Denial of Service properly
Understanding Computer Networking OSI model
Botnets & Stressers for DOS & DDOS
SYN Flood attacks
HTTP Flood attacks
UDP and ICMP Flood attacks
Slowloris attack
LOIC & Js LOIC attack
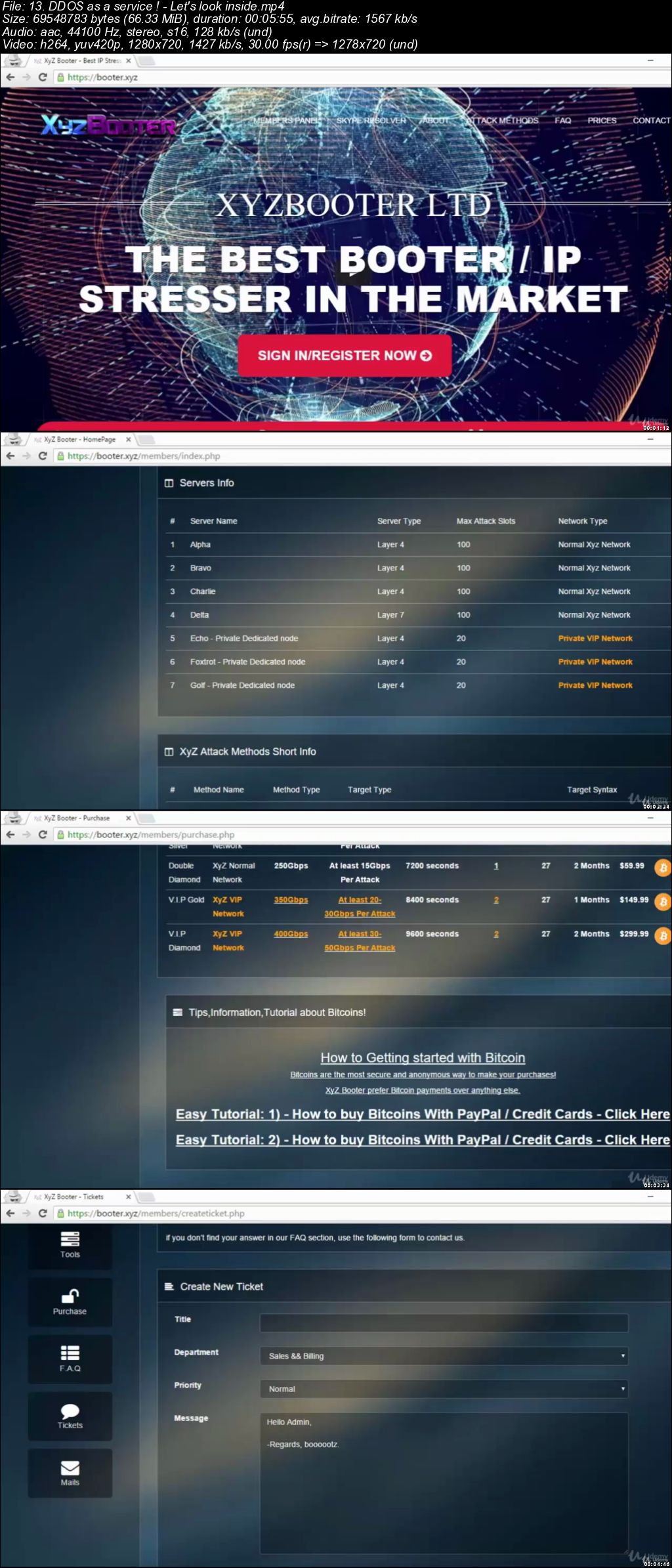
Using DDOS as a service
Practical & Real World examples of DOS & DDOS attacks
Sniff packets using ARP Poisoning
Sniff packets using ARP Spoofing
Learn to do Sniffing attacks using DNS Poisoning
Use flooding , spoofing & poisoning together for Sniffing
Launch advance Man in the Middle attack
Use different tools for Capturing packets
Sniff packets and analyse them to extract important information
Learn to hijack session
Network level session hijacking
Hijacking session using – TCP
Hijacking session using – UDP
Attacking browser for hijacking Session
Web application session hijacking
Brute Forcing for hijacking session
Hijacking cookies of Web application
Using of different tools for automating session hijacking
Using Burp Suite tool
Using OWASP-ZAP & Netsparker
Learn & Understand Cryptography
Using best tools for Cryptography
Learn Social Engineering from Scratch
The Art of Human Attack by Social Engineering
Psychological Manipulation Using Social Engineering
Social Engineering using Kali Linux
Social Engineering using social engineering toolkit
Generate undetectable payload
Uses of Metasploit in Social Engineering
Enumeration using DNS , SNMP , SMTP , NTP , Netbios & more
Advanced Social Engineering
Phishing attack using BEEF & PHISH5
Phishing attack using Spearphishing
Phishing pages & Phishing Emails
Learn how to Scam using Social Engineering
Learn Scamming with Real-World example
Get away with Identity Theft
Buying and Selling identities
Enumerating the target
Enumeration using DNS , SNMP , SMTP , NTP , Netbios & more
Learn Enumeration practically
Learn Buffer Overflow from Scratch
Buffer Overflow using Programming
Buffer Overflow using Malwares
Database Hacking & Reporting using Buffer Overflow
Getting access to the system using Buffer Overflow
Compromising the Victim using Buffer Overflow
Advanced techniques of Buffer Overflow
Mastering Buffer Overflow
Learn Web Application hacking from Scratch
Understand the basic of Web application hacking
Gathering information for hacking web applications
Using different tools for gathering information such as: Nmap , Wget , Burpsuite ..etc
Learn to tamper web application
Cross Site Scripting (XSS) & Cross Site Request Forgery (CSRF) attack on web application
Identity Management & Access Control attack
Basics of Malware such as: definition , types ,destructiveness …etc
Basics of Trojan such as: definition , types ,destructiveness …etc
Creating a Trojan Virus
Infecting the Victim using our Trojan Virus
Evading Anti Virus software using our Trojan Virus
Creating a Virus Worm.
Learn Cloud Computing basics
Hacking through Cloud Computing
Service hijacking via Social Engineering
Economic Denial of Sustainability (EDoS) attack in Cloud Computing
Compromising the victim using Cloud Computing hacking.
Learn to hack systems from Scratch
Cracking Systems using Kerberos , Salting , John the Ripper & much more
Gaining access to the Victim’s system
Escalation & Escalating Privileges
Maintaining access to the Victim’s PC
Creating & Using Backdoors
Creating & Using Keyloggers
Post Exploitation on Victim’s System
Rootkits , Steganography using for Post Exploitation
Covering our tracks
Basic methods for – Clearing our logs & evidence
Advanced methods for – Clearing our logs & evidence.
Learn Website Hacking from Scratch
Learn Cross Site Scripting (XSS) , SQL Injection & Web Server hacking
Understanding Cross Site Scripting (XSS)
Understand untrusted Data Sensation
Understanding input and output encoding
Attacking website with Cross Site Scripting (XSS)
Mounting Cross Site Scripting(XSS) attack
Mounting Clickjacking attack
Extracting Data from SQL Injection
Blind SQL Injection
Learn advanced SQL Injection
Fuzz testing with Burp-Suite
Using SQL map for hacking
Mastering SQL injection.
Web server hacking basics & theory
Discovering vulnerabilities in Web server hacking
Automation of Web Server hacking.
Learn Mobile hacking from Scratch
Android mobile hacking from Scratch
Understanding the architecture of IOS
Hacking IOS device using malware
Hacking IOS mobile using other methods
Hacking other mobile platforms
Hacking mobile devices using malwares
Creating payloads for Android mobile hacking
Social Engineering Attack on Android mobile
Spoofing Emails , Sms , Phone numbers
Attacking with metasploit
Spoofing the Network
Rooting the Device
Using DSPLOIT & Bugtroid
Hacking windows phones
Hacking blackBerry phones
Defending different attacks
Defend Reconnaissance and Footprinting
Defend sniffing attack
Defend enumeration
Defend web application hacking
Defend cloud computing hacking
Defend buffer overflow
Defend Social Engineering
Defend DOS & DDOS
Defend Cross Site Scripting(XSS)
Defend SQL Injection
Learn Digital Forensics from Scratch
Learn about network,mobile,computer,database forensics
Forensic Data Analysis & Evidence Handling
Kali Linux & Forensics
Digital forensics using different tools such as: LIBEWF , Guymager ,DC3DD ,AFFLIB etc..
Learn Python from Scratch
Strings , Function , Function Arguments & more
Making a Web app in Python for clearing our concept
Python & Kali Linux learn for Scratch
Installing WingIDE on kali & WingIDE overview
Writing a TCP client in python
Writing a UDP client in python
Writing a TCP server in python
Developing an application like Netcat
Network scanning using metasploit
Network scanning using OpenVAS & NMAP
Analysing vulnerabilities
Gaining access to the system using Metasploit
Gaining access to the system using Metasploit exploits
Gaining access to the system using Metasploit payloads
Uses of Meterpreter : basic to advanced
Post-exploitation using metasploit
Maintaining access to the system using Metasploit
Advanced uses of Metasploit
Agenda and Payload of metasploits
Creating payload with msfvenom
Attacking SQL server using Metasploit
Pivoting using Metasploit
Requirements
Basic It Knowledge
Description
This is the Platform’s biggest and most advanced Cyber Security course. Black Hat hacking has always been a dream for us! Make your dream come true by taking this Course. Learn to launch Cyber attacks, defending cyber attacks, hacking computer systems/websites like a Real-World black hat hacker & much more!
This is the most comprehensive, yet straight-forward, course for Cyber Security on Udemy! In this course you will start as a beginner with no previous knowledge & by the end of the course you will be at a High Intermediate level.
With 550 lectures & 66+ hours of content this comprehensive course leaves no stone unturned! Once you buy that Course you will get a Life time access to the content & you will get answer to your every single question from an experienced IT professional!
You don’t need any previous programming knowledge or basics for starting this course.In this course we will start from Scratch.We will explain all the techniques of hacking , theory behind those techniques & give Real world examples in every single Part of the course!
In this course there are 18 parts but this course can be divided in to 8 main sections. Below there is a brief explanation of this Complete course.You will learn much more than what we try to explain below !
Main Section One(1) : Brief introduction to the complete course , Setting up the lab & maintaining Anonymity [Covering Part 1]
Complete course overview in just 3 minutes & 39 seconds !
Setting up the Complete Ethical Hacking Lab
1.Learn how to Install VirtualBox
2.Configure the VirtualBox
3.Downloading & Installing Kali Linux latest
4.Downloading & Installing 2 different Operating Systems(Windows & Metasploit)
5.Downloading & Installing Android Platforms on the PC for learning to hack Android mobile phones.
Hacking Lab Basics
1.Kali Linux Basics
2.Basics of Kali Linux Terminal & Commands
3.Advanced uses of Kali Linux Terminal & Commands
4.Getting Black Hat hacking tools for further use(Only for Ethical Hacking purpose!)
Anonymity Online
1.Learn how to be Anonymous Online
2.Learn how to cover your tracks
3.Learn to use different tools for maintaining anonymity Online
4.We are going to get more lectures to be anonymous online through out the Course
Main Section Two(2) : Gathering Information [Covering Part 2]
Gathering Information about the Victim weather it is a person, website or a company.
Gathering Passive Information
1.Gathering Passive Information using different tools
2.Searching for hidden people
3.Hacking Job sites for getting details
4.Using Netcraft for gathering Passive Information
5.Using Maltego for gathering Passive Information
6.Using Google Hacking for gathering Passive Information
7.Knowing about any hidden information easily
Gathering Active Information
1.Gathering active information using search engines
2.Using different websites for Gathering active information
3.Advanced Google Search operators for gathering active Information
4.Using Database Hacking , Tools & advanced Google hacking
5.Nmap, Nmap NSE scripts, Zenmap for gathering Active Information
6.Gathering Active Information using DNS transfer Zone, SMB Null Session & SMB Enumeration
Main Section Three(3) : Hacking WiFi & Wired connection [Covering Part 3]
Understanding how WiFi & Wired hacking works
Identifying the target network
Identifying hidden networks
Exploiting the target network
1.Hacking WEP networks
2.Hacking WPA/WPA2 networks
3.Hacking WPS enabled networks
4.Capturing packets
5.Taking advantage of Router misconfigurations
6.Post Exploitation
Different types of attack on the Victim
1.Non disrupting techniques
2.Eavesdropping
3.Creating an access point for Man in the Middle attack
4.Creating an Online access point for Man In the Middle attack
5.Denial of Service attack (DOS) on the Wireless Network
6.Disconnecting any device from the network
Creating rogue access Point
Creating Fake Captive portals
Covering our tracks
1.Using Disposable VMs for covering our tracks
2.Changing our MAC addresses
Wireless penetration testing Accessories
Main Section Four(4) : All the attacks that a hacker can do and you should learn ! [Covering Part 4 to 15 ]
Scanning Network(Brief Description)
Learn to Scan Networks
Learn to Scan out of your own Network
Network level scanning & Web application level scanning learn both
Learn to Scan for Vulnerability
Get Demonstration & Real World examples
DOS & DDOS attack (Brief Description)
Understand DOS & DDOS properly
Learn about the Computer networking OSI model
DDOS in the world map
Clearing concept using best tools and services
Doing DOS & DDOS using HTTP flood, ICMP flood, SYN flood,Slowloris, LOIC , JS LOIC, etc…
Stressers and Booters for DOS & DDOS
Tools that hacker community use for DOS & DDOS
Sniffing Attacks(Brief Description)
Sniffing using ARP Poisoning & ARP Spoofing
Sniffing using DNS Poisoning
Advanced techniques for Sniffing
Demonstration in every section!
Session Hijacking(Brief Description)
Learn Session Hijacking of Network level & Web Application level
Network Level Session Hijacking using TCP & UDP hijacking, Blind hijacking etc…
Web application level session hijacking using Cookies, Bruteforce, XSS etc…
Automating Session hijacking using Burpsuite, Owaspzap, Netsparker etc…
Social Engineering(Brief Description)
Social Engineering basics
The Art of human attacks using social engineering
Human based Social Engineering vs Computer based Social Engineering
Learn Social Engineering using Kali Linux such as: Creating payloads, listening for it, uses of metasploit etc…
Phishing attacks using SET toolkit, Phish5, Phishing emails etc…
Doing Scams [Learn how to do & take money]
Learn to do Identity theft
Buy & Sell Identities
Real World example included for Social Engineering attack
Enumeration(Brief Description)
Learn & Understand Enumeration
Enumeration using SNMP, SMTP, NTP, NETBIOS, LDAP etc…
Demonstration of Enumeration using SNMP, SMTP, NTP, NETBIOS, LDAP etc…
Buffer Overflow hacking(Brief Description)
Learn to hack using Buffer Overflow
Basics of Buffer Overflow
Mastering Buffer Overflow
Buffer Overflow using Malware
Buffer Overflow using Programming
Database hacking & Reporting of Buffer Overflow
Learning advance techniques of Buffer Overflow
Compromising the Victim using Buffer Overflow
Web Application Hacking(Brief Description)
Learn how to do Web application hacking
Gathering information for application hacking
Learn to do web application tampering
Client side attacks of web application hacking
Identity management & access control of web application hacking
Hacking with Malware(Brief Description)
Learn malware threats from Scratch
Basics of Trojan Viruses
Basics of Virus & Worms
Creating a Trojan Virus
Creating Virus & Worms
Cloud Computing Hacking(Brief Description)
Learn to hack with Cloud Computing
Cloud computing basics
Hacking through cloud computing
Cloud computing using Social Engineering
Strengthening the security of Cloud Computing
DDOS prevention and much more for strengthening the security of Cloud computing
Hacking Systems(Brief Description)
Learn to hack systems step by step
Gaining access attacks
Maintaining access to the Victim’s pc
Post exploitation after gaining access
Covering our tracks & evidence
Main Section Five(5) : Website Hacking & Penetration testing [Covering Part 15 to 16]
Learn how to Cross Site Scripting(XSS) in great details!
Hacking using Cross Site Scripting Demonstration
Learn how to do SQL Injection in great details!
Blind SQL Injection
SQL Map to hack a website
Advanced SQL Injection
Hacking Using SQL Injection Demonstration
Learn how to hack a web server
Web Server hacking advanced techniques
Hacking Web Servers Demonstration
Main Section Six(6) : Learn to hack mobile platforms such as: Android, Windows, Blackberry [Covering Part 17]
Hacking Android phones
Using Payloads, Malwares, Metasploit, Social Enginerering etc… for hacking mobile phones
Hacking IOS mobiles
Hacking Windows mobiles
Hacking Blackberry mobiles
Hacking Demonstration for all the platforms!
Main Section Seven(7) : Defend Hacking attacks & Digital Forensics [Covering Part 18]
Defend most of the attacks that we learnt
Learn forensics from scratch
Learn Kali Linux & Forensics
Using different tools from Digital Forensics such as : LIBEWF, Guymager, DCFLDD, Hasdeep etc…
Main Section Eight(8) : Bonus Sections !
Python & Kali(Brief Description)
Learning Python Programming language from Scratch
Making a Web App with Python for clearing our concept & mastering Python
Python & Kali Linux together
Writing a TCP Client in Python
Writing a UDP Client in Python
Writing a TCP Server in Python
Developing an application like Netcat in Python
Metasploit in Hacking(Brief Description)
Learn Metasploit from Scratch
Scanning using Metasploit
Gaining access to the system using Metasploit
Maintaining access to the System using Metasploit
Learning advanced uses of Metasploit
Who is the target audience?
People who want to learn about Cyber Security
Anybody who is interested in learning ethical hacking & penetration testing
People who want to get a training to become a Certified Ethical Hacker (CEH)
People with basics/advanced level knowledge of Hacking and want to take their knowledge to next level
Anybody who wants to learn how to launch different attacks exactly the same way Black Hat hackers do
Anybody who wants to learn about Website Hacking & Penetration Testing From Scratch
Anybody who wants to learn about Digital Forensics
Anybody who wants to learn Python & Kali Linux
Anybody who wants to grow their skill to get a better job
Anybody who wants to advance their career as a freelancer online & increase their hourly pay rate
Anybody who wants to learn how a hacker would attack their Computer / Websites
Anybody who wants to secure their Computer / Websites
Password/解压密码-0daydown
Download rapidgator
https://rg.to/file/40b775dc8491cc787d08860f8c242d59/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part01.rar.html
https://rg.to/file/5475690c31f5c7a31a4becdbd8eabacd/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part02.rar.html
https://rg.to/file/13596d8fbf43cfdad8a9ca4cb6031234/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part03.rar.html
https://rg.to/file/af7bb6868c36fff2d25692acb49ada87/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part04.rar.html
https://rg.to/file/93e71a29543dd90ff9b27120327a974e/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part05.rar.html
https://rg.to/file/2af0f4c41e8adddc7d72b6efdb968031/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part06.rar.html
https://rg.to/file/26bcfa2fadd0a57d430882145f45926a/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part07.rar.html
https://rg.to/file/d445c09e69d85a611ac86695e024d1e1/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part08.rar.html
https://rg.to/file/96497125431be7355cc5b9fca925eb8f/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part09.rar.html
https://rg.to/file/805c9d65440c39e896b0d088a7c5661f/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part10.rar.html
https://rg.to/file/6d455b800d3ebec8ee117e579420a7bb/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part11.rar.html
https://rg.to/file/b5303b033fff9b82519b4a0e65654ecf/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part12.rar.html
https://rg.to/file/1b2ca663957ee95d85473a49ccc0dc18/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part13.rar.html
https://rg.to/file/cd65cab9366db4f94a8a9f39f1ef1b67/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part14.rar.html
https://rg.to/file/12069b37b8a979a5ff23e639f5b52bf5/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part15.rar.html
https://rg.to/file/2df7fe9cbc1d5d1db0ba7b113f46a658/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part16.rar.html
https://rg.to/file/63c8121b9fccd45704f07d59f64d09e1/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part17.rar.html
https://rg.to/file/e9b267a3ab421c3bc9a03f2a0b1be986/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part18.rar.html
https://rg.to/file/a420b2508a0694155892b919b8a19da0/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part19.rar.html
https://rg.to/file/877cf1492bc83e1e60ce4c82db81a1f6/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part20.rar.html
https://rg.to/file/35d10dec6d7c4e4b3e4f398db344ce4b/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part21.rar.html
https://rg.to/file/291c11cc110ec6860622ef775e532d4a/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part22.rar.html
https://rg.to/file/8ce1414107e58858491a6304708ab002/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part23.rar.html
https://rg.to/file/ab01a17ff89d1d4190303caa10c9aa3c/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part24.rar.html
https://rg.to/file/b268a40e14fe08f26e11035c5a8b9c52/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part25.rar.html
https://rg.to/file/16ed4c215f9a489b2c641d12158bf547/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part26.rar.html
https://rg.to/file/ee59e2665cb0465082fa16a298be5b1e/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part27.rar.html
https://rg.to/file/bf36d6c5c10e9c65b7d418d604b0f597/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part28.rar.html
https://rg.to/file/7ace546b4639b627dc941b48f85ef81e/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part29.rar.html
https://rg.to/file/15b66c4738eccab1591efbc51d309192/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part30.rar.html
https://rg.to/file/0307f4fc7304d9b0ac46f3271c178ddf/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part31.rar.html
https://rg.to/file/92750cc2f071b189726b8aa1c2beb360/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part32.rar.html
https://rg.to/file/4ea606205cb60289904bd5cc464bb799/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part33.rar.html
https://rg.to/file/2886b5dec173af6dad2aa1b8d5d19467/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part34.rar.html
https://rg.to/file/e6ee66f5e78580ffa97d68417ad01169/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part35.rar.html
https://rg.to/file/4b71e754d155679f66c15895580b0518/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part36.rar.html
https://rg.to/file/7aee68d2fee271fb9f2d1c4c6a142b80/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part37.rar.html
https://rg.to/file/b278a20c756dd971d23df5c82daa1ecc/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part38.rar.html
https://rg.to/file/83273f9aa2aa772ed24ecba45889e1de/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced!.part39.rar.html
Download nitroflare
http://nitroflare.com/view/87CC58EE864E5C5/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part01.rar
http://nitroflare.com/view/3B14911F5E1F7EC/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part02.rar
http://nitroflare.com/view/450C784712EAA5C/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part03.rar
http://nitroflare.com/view/C9232885F7FC137/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part04.rar
http://nitroflare.com/view/3856EE44CC8FB85/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part05.rar
http://nitroflare.com/view/9C1CAEBF31A2C3B/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part06.rar
http://nitroflare.com/view/48AD2C7D82E7AC4/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part07.rar
http://nitroflare.com/view/1D50319806E9D7E/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part08.rar
http://nitroflare.com/view/015A4E64E4F4A1F/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part09.rar
http://nitroflare.com/view/D7ED3B81909E3A6/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part10.rar
http://nitroflare.com/view/0CB67B6DAF63AD5/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part11.rar
http://nitroflare.com/view/48607927717ADD5/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part12.rar
http://nitroflare.com/view/4ED1CFB64458F89/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part13.rar
http://nitroflare.com/view/9A5DA40475BEAC7/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part14.rar
http://nitroflare.com/view/8BC2464182C2958/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part15.rar
http://nitroflare.com/view/5C58EC1278967D3/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part16.rar
http://nitroflare.com/view/93C07F94A0575EF/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part17.rar
http://nitroflare.com/view/FB2357BE42B5D96/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part18.rar
http://nitroflare.com/view/43F620CD58E9DB4/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part19.rar
http://nitroflare.com/view/D656DE2EB52FA35/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part20.rar
http://nitroflare.com/view/0A32C31A7C553FA/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part21.rar
http://nitroflare.com/view/299F5CD498E5D6F/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part22.rar
http://nitroflare.com/view/5BCC5E088F161D3/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part23.rar
http://nitroflare.com/view/5FA240C484EB9E5/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part24.rar
http://nitroflare.com/view/EDCFAD70846A380/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part25.rar
http://nitroflare.com/view/EB01C3FF300569B/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part26.rar
http://nitroflare.com/view/560220DEE072C26/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part27.rar
http://nitroflare.com/view/4A794FF6A36B778/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part28.rar
http://nitroflare.com/view/AAA1D54222E64A4/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part29.rar
http://nitroflare.com/view/714EB4F8FF2BB2B/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part30.rar
http://nitroflare.com/view/33B193B9FCE7ACA/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part31.rar
http://nitroflare.com/view/B370BB76D67908E/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part32.rar
http://nitroflare.com/view/0926096D4E784DE/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part33.rar
http://nitroflare.com/view/01D8DBFB8D50599/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part34.rar
http://nitroflare.com/view/CAFFFF94599947F/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part35.rar
http://nitroflare.com/view/7C0E9C2EF135B47/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part36.rar
http://nitroflare.com/view/DB56E5BF10AA38B/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part37.rar
http://nitroflare.com/view/A05B409C706A699/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part38.rar
http://nitroflare.com/view/0742316EFC8AAE0/The_Complete_Cyber_Security_Bundle_Beginner_to_Advanced%21.part39.rar
Download 百度云
你是VIP 1个月(1 month)赞助会员,
转载请注明:0daytown » The Complete Cyber Security Bundle: Beginner to Advanced!